Authentication, according to Wikipedia, is the act of confirming the truth of an attribute of a single piece of data claimed true by an entity. Something that has been at the core of systems since the beginning has evolved over the years and like the rest of development has increased in complexity as well.

Authentication perhaps started with a simple email and password. To this day, it is used in a majority of systems wherein we rely on users to use a unique password for accessing an application such as email.
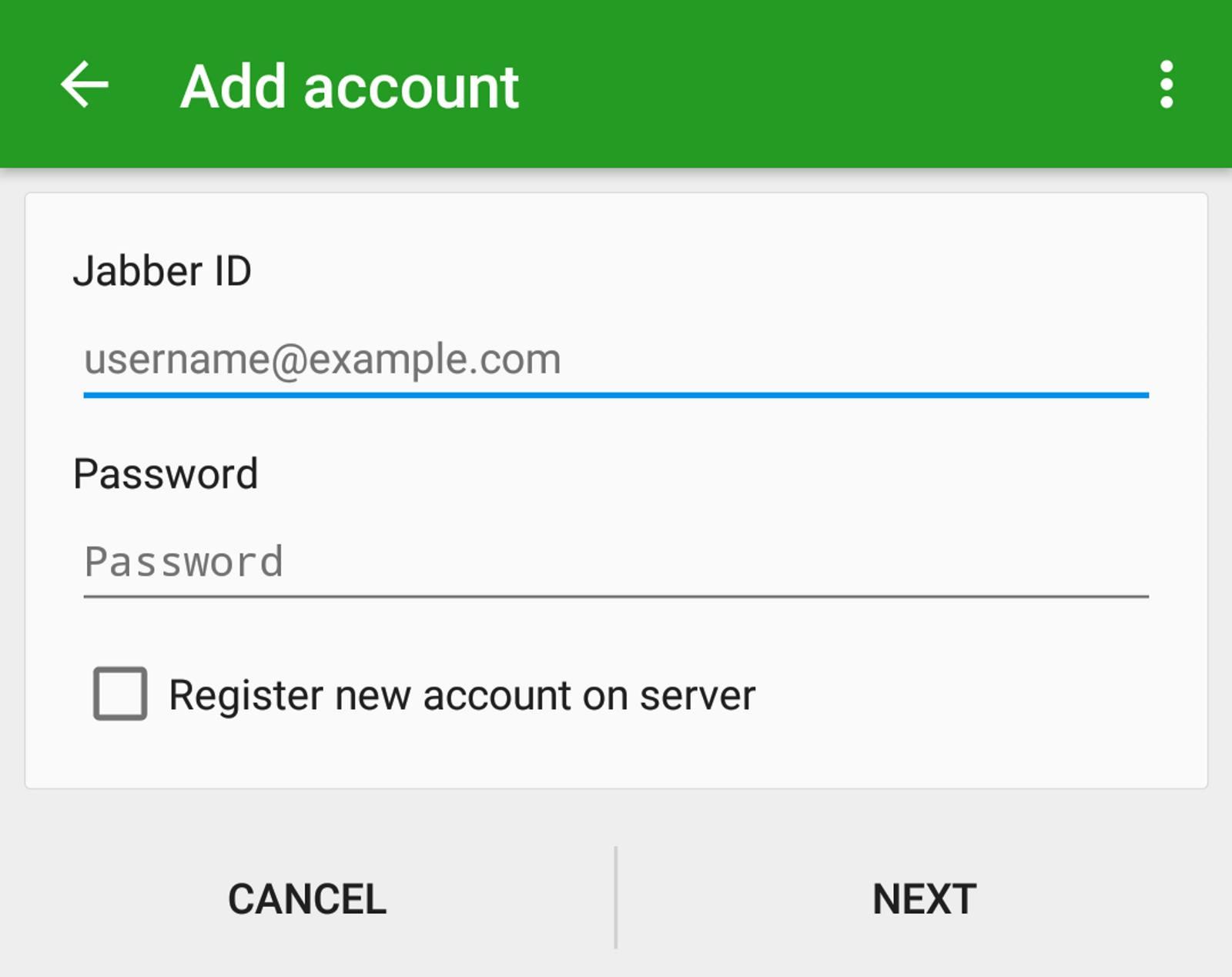
We all know how that turned out to be — people to this day keep the same repetitive passwords such as password, 123456 and qwerty. Furthermore, people generally tend to keep the same passwords everywhere, so if one system is compromised, the others are too — With more accounts being created every day, this posed a serious security risk
Enter Two-Factor Authentication
To authenticate a user with more than one way, 2-Factor authentication came into the picture. This can now be accomplished by:
- Asking security questions (Apple ID)
- Sending a sign-in link (Slack’s magic link)
- Send a TOTP to the email (Microsoft, Skype)
- Send a TOTP to the registered mobile (HDFC Bank)
- Send a notification on the mobile (Google Apps for Work)
- Using a TOTP generator such as Google Authenticator (AWS, Google, etc.)
- Using a random number generator RSA based physical keychain

Each of the company chose a different authentication mechanism due to different user behaviours, legal requirements and expectations and defined the user experience aka UX. For more secure environments, multi-factor authentication was used in combination (e.g. mobile + email) and conjunction with the ones mentioned above:
- Biometrics such as fingerprints, retina scans
- Using a physical card such as a credit/debit card number and CVV
*And then something disruptive happened, social login was introduced — this changed things (and even complicated them)
Many systems added the social logins of Facebook and Google (now available with a wide variety such as Twitter, LinkedIn, Github and Atlassian) but didn’t consider as to what would happen to users existing in the system.
I personally had very bad experiences when instead of taking the email address from my social account and mapping with their own database, they would just create a whole new account and there would be no way to merge the two accounts. The whole point of not remembering a password was defeated.
Gradually systems evolved and made the much-needed fixes. Still, different systems behave differently such as Trello, which allows either log in with email and password or with Google but not with both — and I wonder why!
These days, I use the google password suggest feature but preferably use the google auto login feature
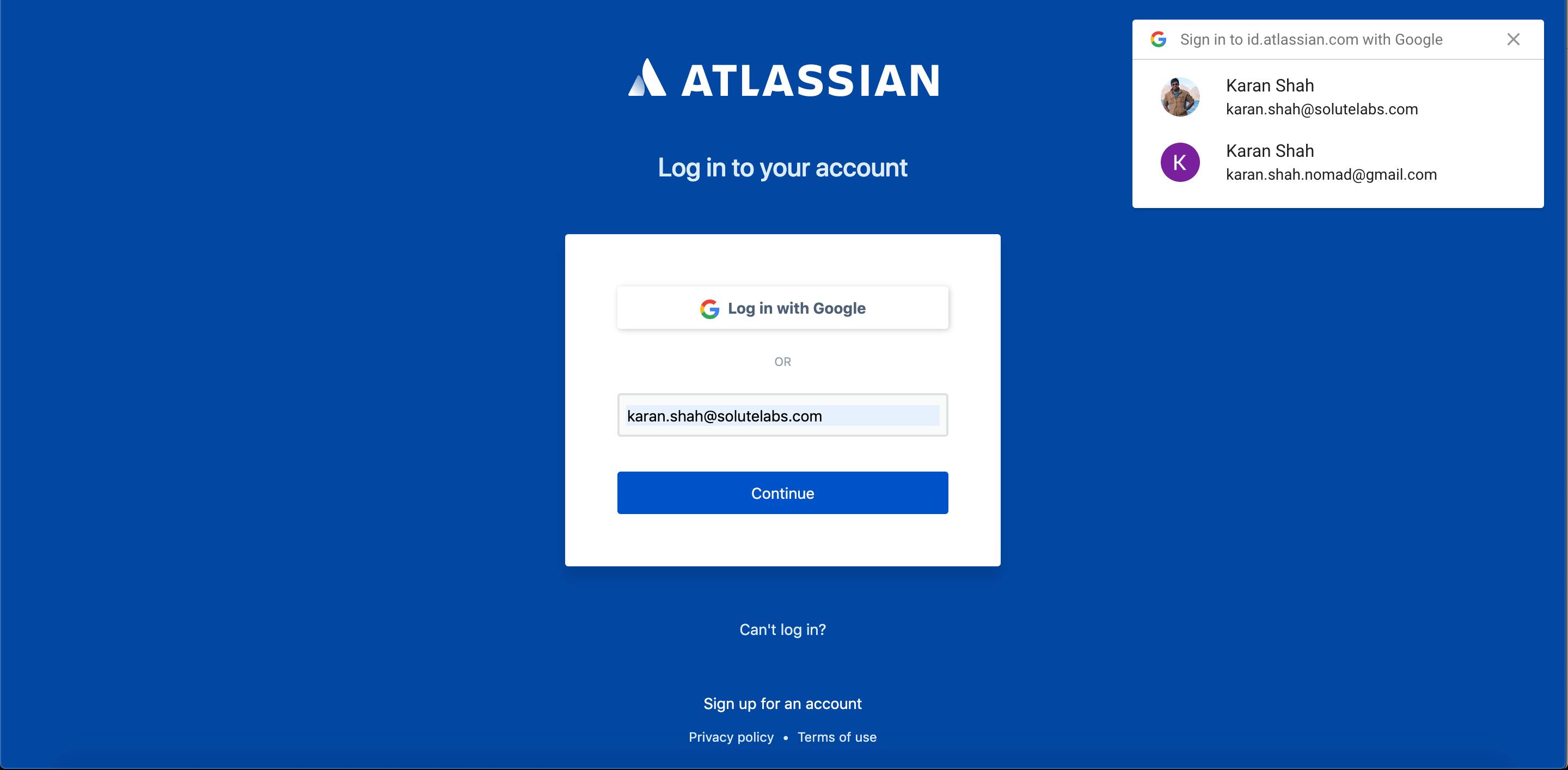
This is available in a large number of websites as well as mobile apps. It helps to stay within the Google ecosystem even if you’re a Mac user.
Another great of login is to just use a mobile number to log in with a TOTP such as Swiggy
Let me know which authentication mechanism do you prefer and why!
About me: I’m the co-founder of Solutelabs, a full-service digital agency focusing on delivering great experiences and developing web and mobile apps that are used by Millions.