Demonstration of EC2 Execution Roles in Practice
First, some introduction and context
This is my first article, and also a relatively short one. I have plans for a much longer article in future, but it will require some context and therefore will be doing first a number of smaller articles for easier reference in the future.
I am also passionate about cloud computing and especially the whole concept of serverless. Therefore, my articles will have a strong cloud focus and I hope it will provide some insights to those who would like to take their solutions to the cloud.
As a starting point, I decided to have a very quick look into Amazon AWS EC2 instance Execution Roles. The official documentation does give some insights but I thought I would demonstrate with some additional examples how effective this approach from AWS is.
Prerequisites
You should be familiar on how to launch an EC2 instance and have some basic experience in the AWS Console. The aim of this article is not to introduce AWS, but rather a practical example of how to use a very specific feature.
What Use is a EC2 Execution Role
An execution role is essentially a policy (or policies) attached to a running EC2 instance that will allow access from the EC2 instance to other AWS resources through the official AWS CLI or SDK.
Managing Your Risk
One of the biggest advantages of this approach is that you do not have to create and share IAM user credentials. It is of course possible to take IAM user credentials and use it in an EC2 instance, but there are several risks to consider.
Here are some risks you need to consider:
- The process of creating and distributing your IAM credentials might not be properly secure and you risk exposing your credentials to unauthorised users
- With credentials stored on the EC2 instance, other users logging onto the instance may have unauthorised access to the credentials
- Any exposure of the credentials, even to authorised users, may allow those users to copy the credentials and use it elsewhere, for example on their personal laptop. In the case where such a user was an employee that no longer work for you, you may be unaware that they still have access.
HOWTO use an EC2 Execution Role - a Practical Example
Below is a simple diagram that demonstrates a practical example of an EC2 instance requiring access to to AWS Secrets Manager.
The basic steps:
- Create a IAM role called "ec2-dark-secret-demo-role"
- Attache a policy called "dark-secret-read-policy" to the IAM role
- Create an EC2 instance and attach the IAM role to it
- Profit!
The most important configuration (the policy definition) as well as a test from both the AWS CLI and the Python Boto3 library are shown:
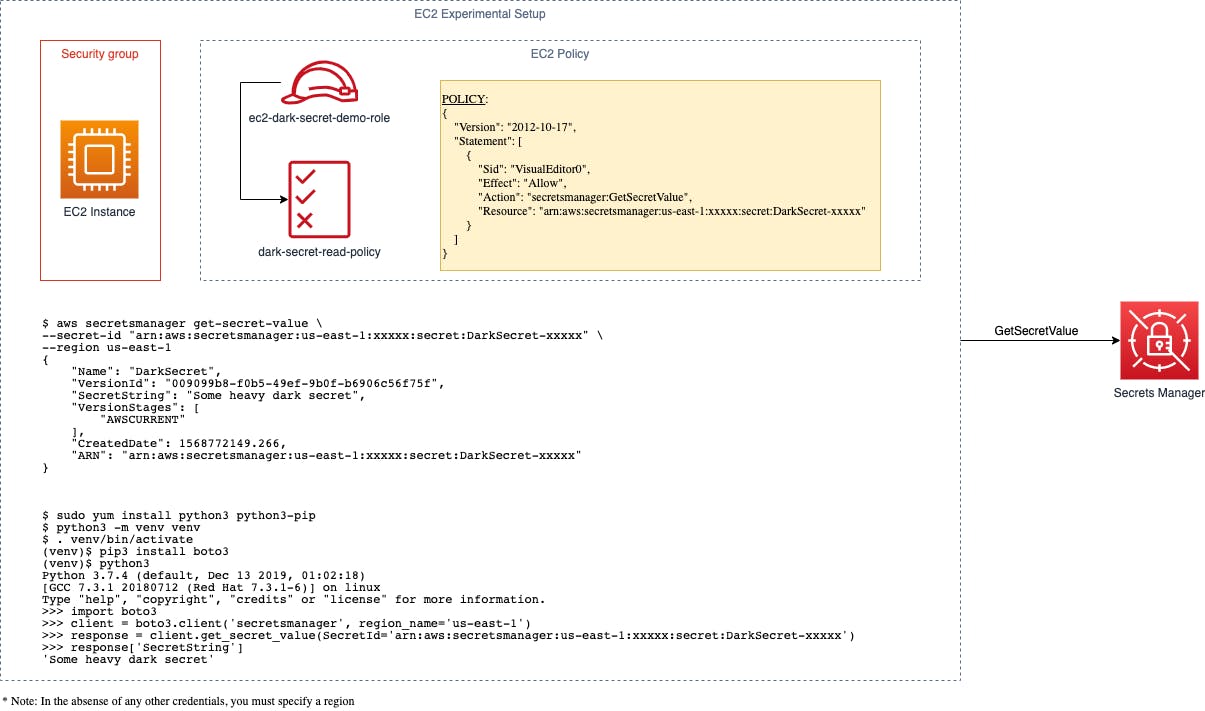
note: You may need to open the image in a new tab to view it full size
Conclusion
This was a quick demonstration of how to use EC2 Execution Role to access an AWS Service (Secrets Manager in this case).