Free Open Source Vulnerability Management Tools That Every Developer Should Know.
When you are working on, or are contributing to an open-source project, one of your primary concerns should be about how secure and safe your open-source code is. Cyber-criminals are consistently looking for new ways to target people and with how delicate open-source code can be, it is very easy for a coder to accidentally program a vulnerability into their repository. The notification and elimination of these vulnerabilities is key to keeping users and programmers safe when making use of an open-source project.
Even though security is imperative for your open-source project, some of the paid developer tools for vulnerability management can be very expensive and some smaller projects may not have the budget to use them. This is why, in this article, we will be helping you to explore free alternatives for developer tools that will allow you to secure your open-source projects, without having to drain your bank account. A number of the developer tools will have both paid and free versions and we will also be exploring the pros and cons of each developer tool so that you can get the best option for your project.
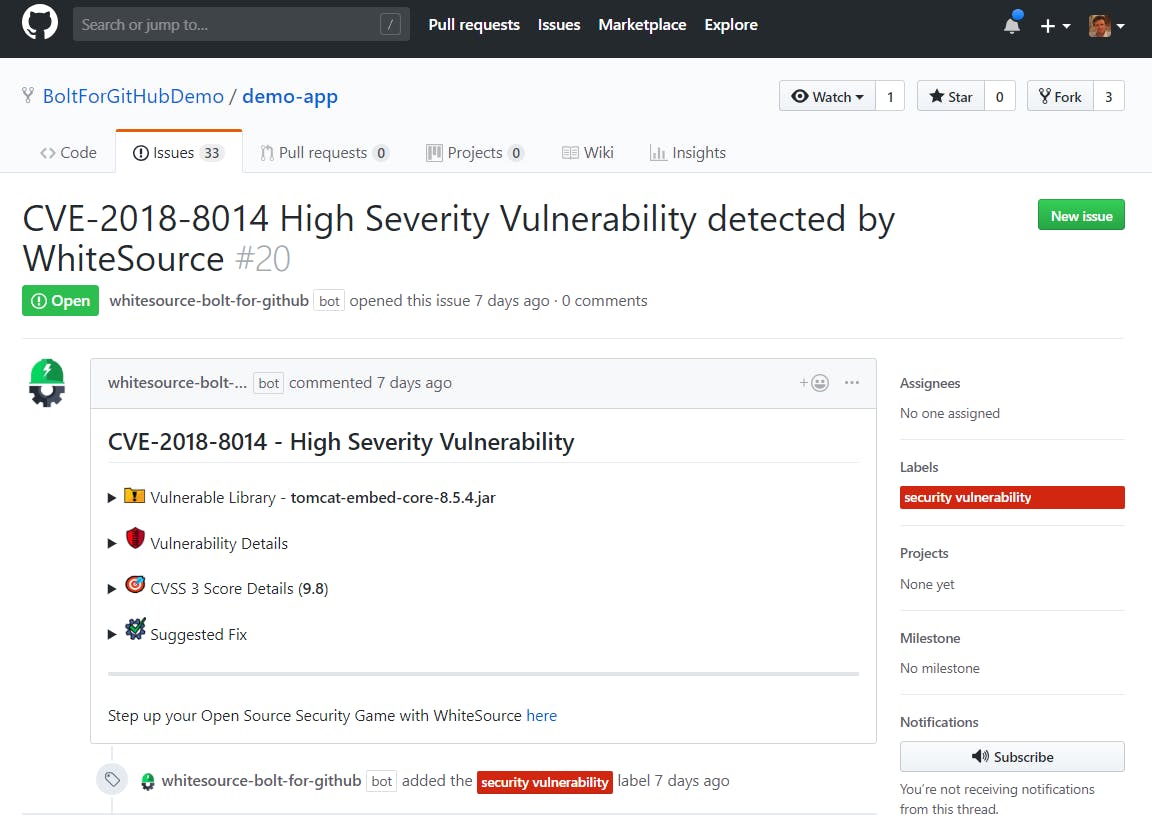
WhiteSource Bolt is a freemium developer tool, that helps to assist their users with identifying and dealing with any open source vulnerabilities that may appear in their code. This developer tool is provided by the company WhiteSource Software, which has been operating in the open-source security market since 2011. This level of experience in their field has provided them with cutting-edge knowledge and this is reflected in the depth of their developer tool.
Bolt is actually two products - one for GitHub users and one for Azure DevOps users., In both cases, Bolt displays its data directly in GitHub/Azure DevOps interface.. Consequently, Bolt scans your software for open source vulnerabilities, whilst simultaneously suggesting fixes that will usually take the form of version updates. You will also be able to see all of your open-source libraries and their respective licenses. The benefit of WhiteSource Bolt is that you will also gain access to their large vulnerability database, which many experts say is the most extensive on the market.
The information that WhiteSource will give you on vulnerabilities is also incredibly detailed. You will have access to the CVE’s description, detailed CVSS scores, validated fixes, and reference links.
WhiteSource Bolt is a very flexible application, supporting over 200 different programming languages.
AppArmor itself is a Linux-specific security app that assists its users with runtime protection and Mandatory Access Control (MAC). Better yet, AppArmor is completely open-source, meaning users do not have to fork out large amounts of money to reap the benefits from it.
Within the security community, AppArmor is strongly considered to be a very beginner-friendly tool, even being compared to a more simplistic version of SELinux, with both applications being very similar. Users are only required to familiarize themselves with the syntax for the system’s profile language and then, they will be able to activate their editor and begin working.
The application allows the administrators in a development project to attach a security profile to each individual program within the system. This includes items such as filesystem access, any network features, and more. The specific niche of AppArmor is that it acts as a MAC system, which means that it will attempt to stop any prohibited actions from occurring, although it also has the capability to inform users of any attempts to violate profile security measures.
Another benefit of AppArmor is that the project itself is also open-source, allowing contributions from a wide variety of developers. These contributions are checked before patches are released and it allows the developer community to be involved heavily in the project, leading to a better end product for users of the app.
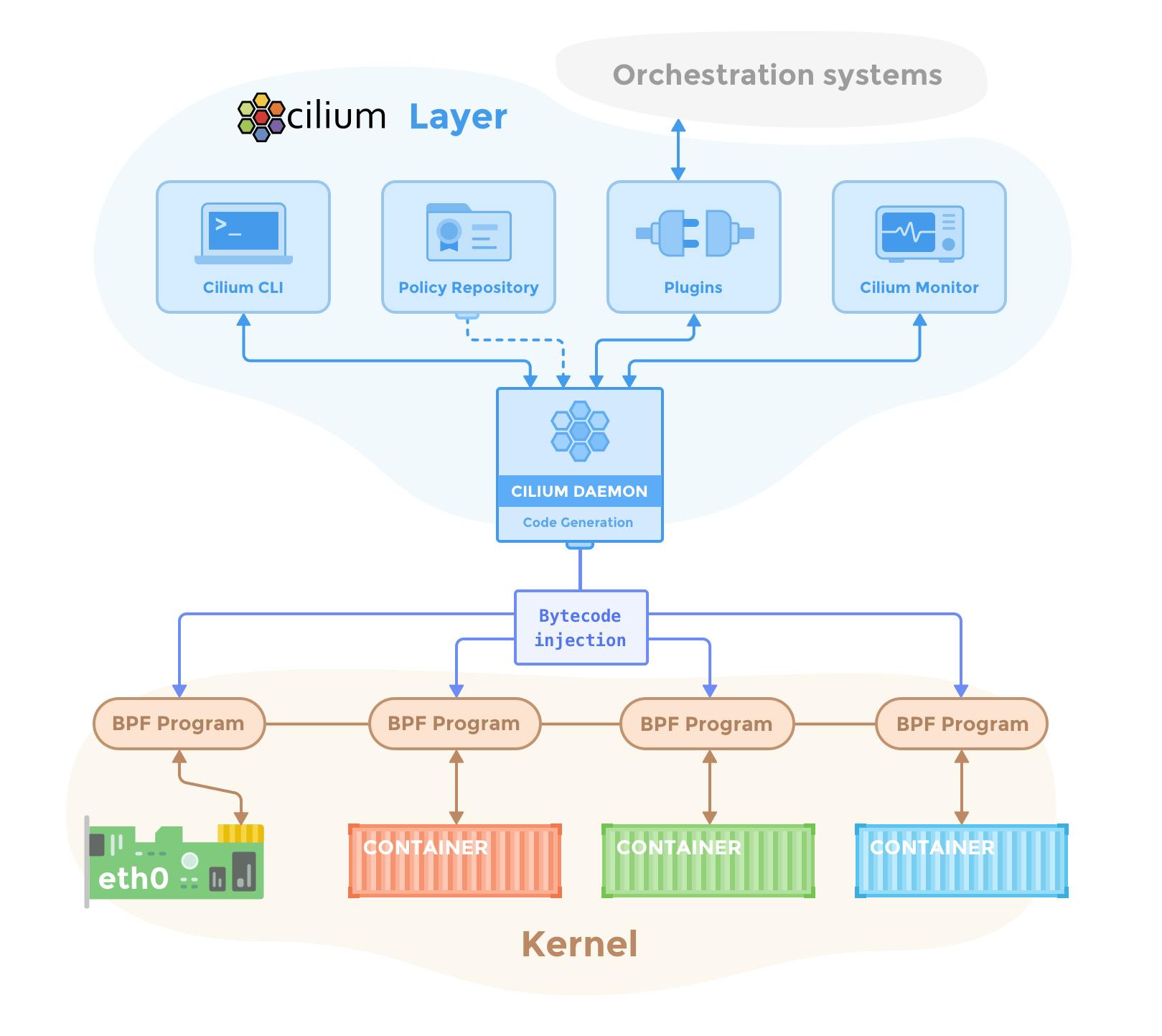
Cilium is an open-source application, which serves the purposes of defining and enforcing application layer and network-layer security policies for its users. Cilium is designed to secure Linux container frameworks like Docker and Kubernetes.
Cilium works by providing its users with transparent security between container applications. The technology itself was originally based off of the new Linux kernel technology, eBPF. The application gives users the ability to create network and HTTP policies, whilst also giving the user the ability to enforce them. These policies would be based on the container or pod identity.
Another feature of Cilium is that it can utilize BPF to filter data paths, conduct monitoring activities, redirection and mangling. Access to these features is available with Linux kernel version past 4.8.0.
Cilium itself is written in and supports the C programming language, with the use of their LLVM compiler back end facilitates writing in C and allows it to be compiled into BPF instructions.
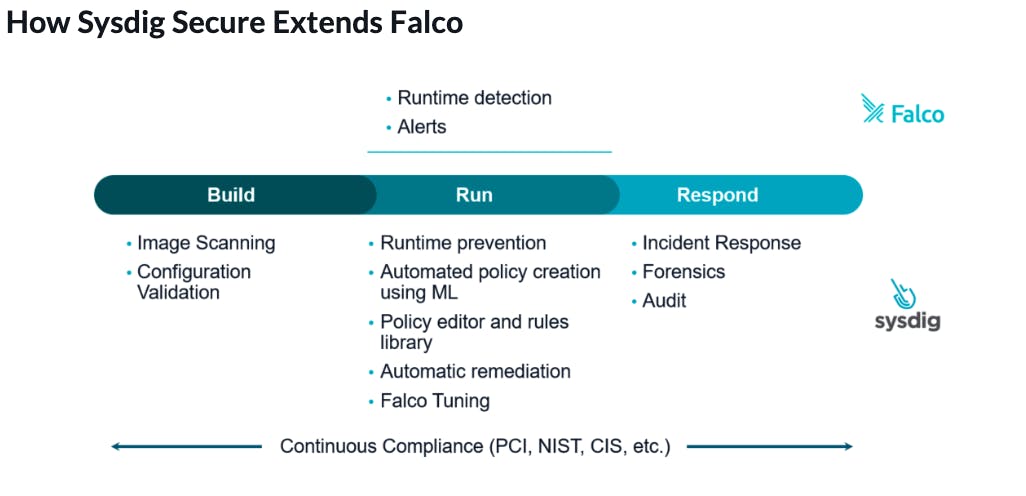
Falco itself is an open-source tool, used by developers to assist with runtime alerting and system forensics. It achieves this through the use of behavioral monitoring software, which can be used to detect any suspicious activity in your development environment. This application is based on technology derived by the company Sysdig, who created Falco. The application itself can also be used to detect intruders on all Linux hosts.
In comparison to tools such as enforcement tools for developers, Falco is more similar to an auditing tool. It works by running in the development user-space and uses a kernel module to access system calls and makes use of similar technology to provide filtering and monitoring actions on the kernel level. Users of Falco are able to set rules on what is normal for their system, which in turn will allow Falco to monitor said system, providing a notification to users whenever anomalous activity is detected.
One of the main benefits of Falco is that it can easily be merged and integrated with other systems, like Docker and Mesos. This allows Falco to make use of and incorporate items such as Metadata and tags from these different systems, providing a much more comprehensive solution for developers.
Falco is written in and supports the use of the C and C+ programming languages.